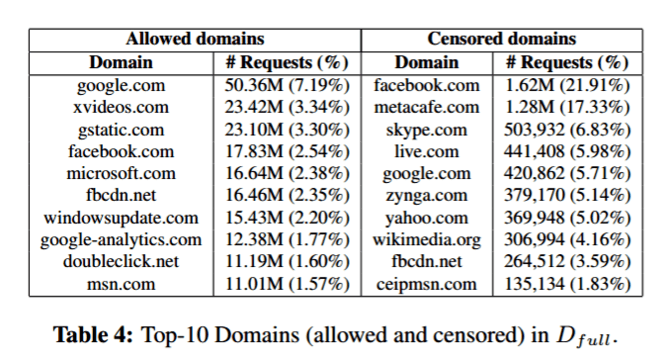
Syria’s brutal Assad government uses censorware from California’s Blue Coat System as part of its systematic suppression of dissent and to help it spy on dissidents; 600GB of 2011 logs from Syria’s seven SG-9000 internet proxies were leaked by hacktivist group Telecomix and then analyzed by University College London’s Emiliano De Cristofaro.
The appliances were sometimes misconfigured, meaning the filter caused some collateral damage – for instance, all requests with the keyword “proxy” were blocked, probably in an effort to curb the use of censorship-evading proxies, but this also had the effect of blocking adverts and certain plug-ins that had no relation to banned content.
We found that Syrian users did try to get around the filters, using tools such as Tor, or virtual private networks (encrypted tunnels between two computers using the public internet), and that these were fairly effective. We also noticed that some tools not necessarily designed with circumventing censorship in mind could also be used to access blocked content – for example using peer-to-peer programs such as BitTorrent to download blocked software (such as Skype) and using Google Cache to access (over HTTPS) cached and mirrored versions of blocked web pages.
Lessons On Censorship From Syria’s Internet Filter Machines [Emiliano De Cristofaro/Techdirt]
(Thumbnail: CAT5 Cable, nrkbeta, CC-BY-SA)